Bourne again Shell Bash Remote Code Execution Vulnerability
![]()
HIRT-PUB14011: GNU Bourne-Over again Shell (Fustigate) 'Shellshock' issue in Hitachi products
(VU#252743, CVE-2014-6271, CVE-2014-7169)
1. Overview
GNU Bourne-Once again Shell (Bash) contains a vulnerability that could permit an attacker to remotely execute shell commands by attaching malicious lawmaking in environment variables used by the operating system. This vulnerability is ordinarily referred to equally "Shellshock".
September 24, 2014
GNU Bash vulnerability (CVE-2014-6271) in environment variables parsing was disclosed to the public. Security update for GNU Fustigate vulnerability (CVE-2014-6271) has been released for about major Linux distributions.
September 25, 2014
GNU Fustigate Incomplete Prepare Remote Code Execution Vulnerability (CVE-2014-7169) was disclosed to the public.
September 26, 2014
Security update for GNU Bash vulnerability (CVE-2014-7169) has been released for most major Linux distributions. Too, Carmine Hat reported "Out of Bounds Retentiveness Access Denial of Service Vulnerability (CVE-2014-7186)" and "Off-By-One Error Denial of Service Vulnerability (CVE-2014-7187)".
September 27, 2014
GNU Bash Incomplete Prepare Remote Code Execution Vulnerability (CVE-2014-6277 and CVE-2014-6278) was disclosed to the public.
CVSS Severity
CVE-2014-6271: GNU Bash Remote Code Execution Vulnerability
CVE-2014-7169: GNU Bash Incomplete Fix Remote Code Execution Vulnerability
CVE-2014-7186: Out of Premises Retentivity Access Deprival of Service Vulnerability
CVE-2014-7187: Off-By-I Error Denial of Service Vulnerability
CVE-2014-6277: GNU Bash Incomplete Fix Remote Lawmaking Execution Vulnerability
CVE-2014-6278: GNU Fustigate Incomplete Fix Remote Code Execution Vulnerability
Base of operations Metrics: 10.0
Admission Vector: Network
Admission Complexity: Depression
Authentication: None
Confidentiality Impact: Complete
Integrity Touch on: Consummate
Availability Impact: Consummate
Temporal Metrics 8.vii (September 27, 2014)
Exploitablity: High
Remediation Level: Official fix
Report Confidence: Confirmed
- http://nvd.nist.gov/cvss.cfm?calculator&version=ii&vector=(AV:N/Ac:Fifty/Au:N/C:C/I:C/A:C/Due east:H/RL:OF/RC:C)
ii. Affected Systems
+ GNU Fustigate through 4.iii
+ Linux, BSD, and UNIX distributions that utilise GNU Bash
+ Hitachi Products that utilize GNU Bash
3. Affect
By attacking a service that uses a vulnerable version of GNU Bash, a remote, unauthenticated attacker may be able to execute crush commands past attaching malicious code in environs variables used past the operating system.
Web application
CGI scripts are likely afflicted by this issue: when a CGI script is run past the web server, it uses environment variables to pass data to the script.
Secure Vanquish (SSH)
This effect can be used to execute any command to bypass the restricted command command.
DHCP client
DHCP client uses various environment variables and runs Bash to configure the network interface. Connecting to a malicious DHCP server could allow an attacker to remotely execute arbitrary commands.
Mail server
qmail uses various environment variables to refer the value of mail from: and rcpt to:. This can be used to execute arbitrary commands by specially crafted surround variables.
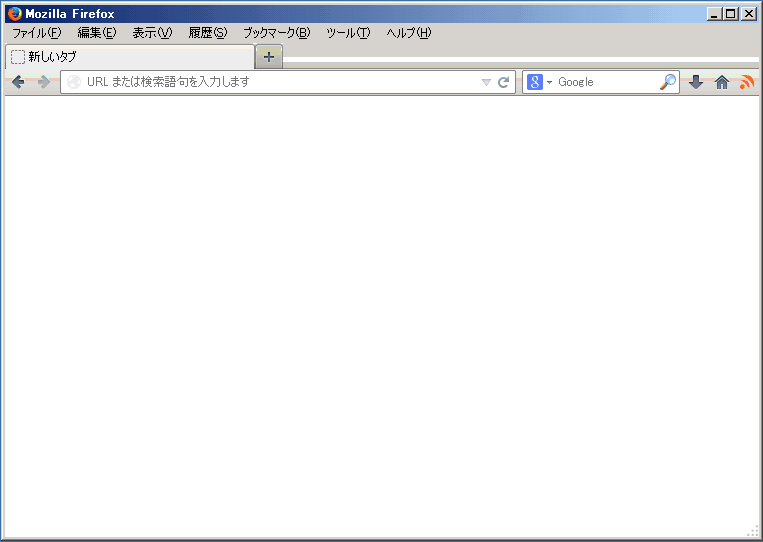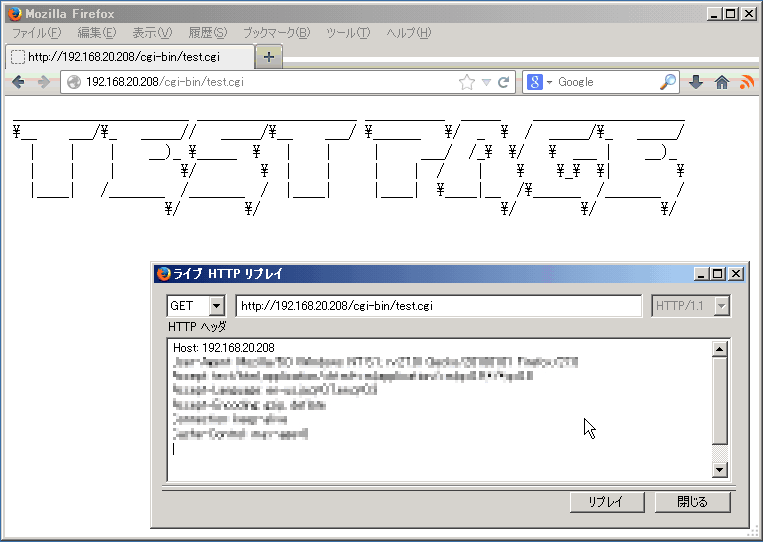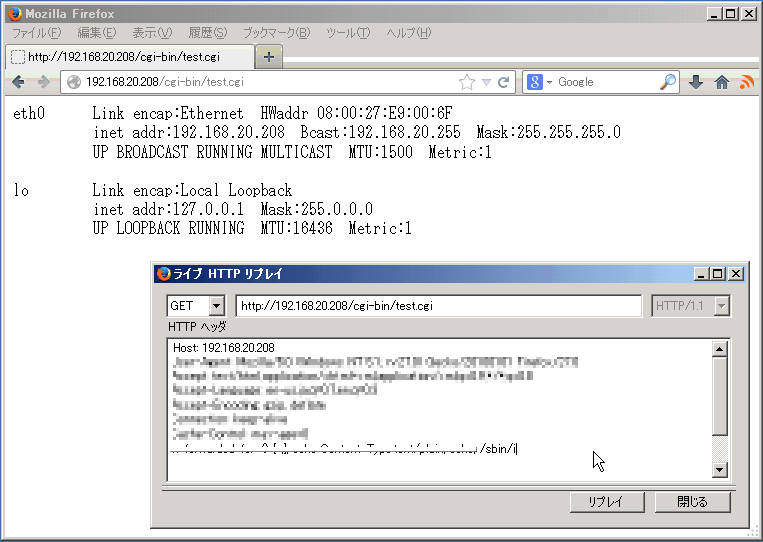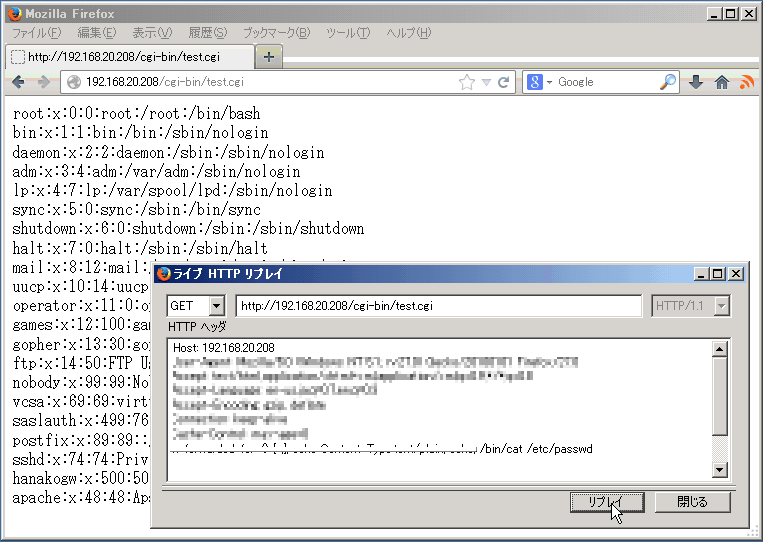
Figure 1. (Example) Capricious beat out commands execution by specially crafted environment variables.
4. Solution
Employ an update
This upshot is addressed in GNU Fustigate. Followings are security update of Linux distributions. Besides, delight refer to the advisories in "five. Product Data" of Hitachi.
- CentOS
- CVE-2014-6271
[CentOS] Critical update for bash released today.
http://lists.centos.org/pipermail/centos/2014-September/146099.html
- CVE-2014-7169
[CentOS-announce] CESA-2014:1306 Important CentOS v bash Security Update
http://lists.centos.org/pipermail/centos-announce/2014-September/020591.html
[CentOS-denote] CESA-2014:1306 Important CentOS 6 bash Security Update
http://lists.centos.org/pipermail/centos-announce/2014-September/020593.html
[CentOS-announce] CESA-2014:1306 Important CentOS 7 bash Security Update
http://lists.centos.org/pipermail/centos-announce/2014-September/020592.html
- CVE-2014-6271
- Debian
- CVE-2014-6271
DSA-3032-ane bash -- security update
https://world wide web.debian.org/security/2014/dsa-3032
- CVE-2014-7169
DSA-3035-i fustigate -- security update
https://www.debian.org/security/2014/dsa-3035
- CVE-2014-6271
- Red Lid
- CVE-2014-6271
RHSA-2014-1293 Critical: fustigate security update
https://rhn.redhat.com/errata/RHSA-2014-1293.html
RHSA-2014-1294 Critical: bash security update
https://rhn.redhat.com/errata/RHSA-2014-1294.html
RHSA-2014-1295 Critical: fustigate Shift_JIS security update
https://rhn.redhat.com/errata/RHSA-2014-1295.html
- CVE-2014-7169,CVE-2014-7186,CVE-2014-7187
RHSA-2014-1306 Important: bash security update
https://rhn.redhat.com/errata/RHSA-2014-1306.html
RHSA-2014-1311 Important: fustigate security update
https://rhn.redhat.com/errata/RHSA-2014-1311.html
RHSA-2014-1312 Critical: bash Shift_JIS security update
https://rhn.redhat.com/errata/RHSA-2014-1312.html
- CVE-2014-6277,CVE-2014-6278
Resolution for Bash Code Injection Vulnerability via Peculiarly Crafted Environment Variables (CVE-2014-6271, CVE-2014-7169, CVE-2014-7186, CVE-2014-7187, CVE-2014-6277, CVE-2014-6278) in Crimson Chapeau Enterprise Linux
https://access.redhat.com/solutions/1207723
- CVE-2014-6271
- Ubuntu
- CVE-2014-6271,CVE-2014-7169
USN-2363-ane: Fustigate vulnerability
http://world wide web.ubuntu.com/usn/usn-2363-i/
USN-2363-2: Bash vulnerability
http://www.ubuntu.com/usn/usn-2363-2/
- CVE-2014-7186,CVE-2014-7187
USN-2364-one: Fustigate vulnerabilities
http://world wide web.ubuntu.com/usn/usn-2364-ane/
- CVE-2014-6271,CVE-2014-7169
v. Production Information
Oct vi, 2014
+ AlaxalA Networks AX serial <Products Confirmed Not Vulnerable>
[AX8600R/6700S/6600S/6300S, AX4600S/3800S/3600S/2400S]
[AX7800R/7700R/7800S/5400S]
[AX2500S/2200S/1200S]
[AX620R]
Oct three, 2014
+ Hitachi Advanced Server HA8000 series <*>
+ Hitachi Avant-garde Server HA8500 series <*>
+ Client Blade FLORA bd100/bd500 series <*>
+ Sparse Client FLORA Se210/Se330 series <*>
+ Hitachi bd Link <*>
+ Entry grade disk array model BR1200 <*>
+ Tape Library L1/8A, Threescore/24, Lx/30A, Sixty/48, L20/300, L18/500, L56/3000, L64/8500 <*>
+ Hitachi UPS/Management software/Hitachi UPS option, PowerMonitor H, PowerMonitor H for Network,
SNMP interface menu, Deejay interface card, SNMP+Deejay interface card <*>
+ Brandish/Keyboard unit/Switch Panel Unit of measurement <*>
+ Hitachi Server Navigator Update Managing director, Log Collect, Log Monitor, Live Monitor, RAID Navigator <*>
+ Hitachi Server Navigator Installation Banana <*>
<*>: <Products Confirmed Non Vulnerable>
- Bear upon of GNU Bash vulnerability (CVE-2014-6271, CVE-2014-7169 and related CVEs) [Japanese]
October 1, 2014
+ Hitachi Metals Switch Apresia serial <Products Confirmed Non Vulnerable>
+ Hitachi Metals XLGMC/XGMC/GMC/GMX/eWAVE/BMC/GMA series <Products Confirmed Not Vulnerable>
- HCVU000000016: GNU Bash vulnerability in environment variables parsing [Japanese]
September xxx, 2014
+ Hitachi Open Middleware Products <Products Confirmed Not Vulnerable>
+ Hitachi Storage Products
+ VFP(Hitachi Virtual File Platform)
- Solution of GNU Fustigate vulnerability (CVE-2014-6271, CVE-2014-7169 and related CVEs) [Japanese]
+ Virtage(BladeSymphonyBS2000/BS500/BS320/BS1000 serial)
- Solution of GNU Fustigate vulnerability (CVE-2014-6271, CVE-2014-7169 and related CVEs) in Virtage [Japanese]
7. Update history
- October 7, 2014
-
- This webpage was newly created and published.
Masato Terada (HIRT) and Naoko Ohnishi (HIRT)
- page top
Source: https://www.hitachi.com/hirt/publications/hirt-pub14011/index.html
Enregistrer un commentaire for "Bourne again Shell Bash Remote Code Execution Vulnerability"